 As you might have noticed this site uses HTTPS. Obtaining SSL certificates was always a bit of a hassle. Finding a certificate authority, doing regular payment, renewals and installing the certificate on your server. Let’s Encrypt is an initiative to provide a better way of enabling encryption on websites. It is open, automated and above all: it offers free SSL certificates. Learn to use Let’s Encrypt on an ISPConfig 3.0 server.
As you might have noticed this site uses HTTPS. Obtaining SSL certificates was always a bit of a hassle. Finding a certificate authority, doing regular payment, renewals and installing the certificate on your server. Let’s Encrypt is an initiative to provide a better way of enabling encryption on websites. It is open, automated and above all: it offers free SSL certificates. Learn to use Let’s Encrypt on an ISPConfig 3.0 server.
I assume you already have an ISPConfig server up and running. You might have a number of sites that use plain HTTP of HTTPS that you want to secure with free SSL certificates. That’s good, we’re going to do the following:
- Obtaining certbot
- Requesting free SSL certificates
- Configuring SSL in ISPConfig
- Enabling automatic periodical renewal
Note: ISPConfig 3.1.1 features automatic installation of Let’s Encrypt certificates. This article was written for ISPConfig 3.0 but still applies to ISPConfig 3.1 as an alternative way (with more control) to integrate ISPConfig with Let’s Encrypt. If you are using the built-in Let’s Encrypt support it is not necessary to run the update script listed in this article.
Obtaining letsencrypt certbot
First of all, obtain the certbot helper scripts and binaries. Certbot is the name of what previously was called the letsencrypt application.
Method 1: Clone the Git repository
If you do not have Git installed, either do it now or use the second method.
Installing git in Ubuntu/Debian
sudo apt-get install git
Installing git in CentOS/RedHat
sudo yum install git
When the installation is completed, navigate to a folder to put the certbot files into, for example, your home-folder.
cd ~ git clone https://github.com/Certbot/Certbot cd Certbot
Method 2: Download the zipped repository
Download and extract the files. You can do this easily using the command line if you have wget and zip utilities available:
wget https://github.com/certbot/certbot/archive/master.zip unzip master.zip mv certbot-master Certbot cd Certbot
Requesting free SSL certificates
We are going to request a certificate for our website wow-doge.com with subdomain amaze.wow-doge.com.
./certbot-auto certonly -w /var/www/wowdoge.com/web -d wowdoge.com -d www.wowdoge.com -d amaze.wowdoge.com
No some real magic is going to happen: the certbot-auto script will setup all requirements and when it is finished it will ask you how to validate the selected domain. Choosing ‘Apache Web Server’ is the easiest but placing files in the webroot works as well.
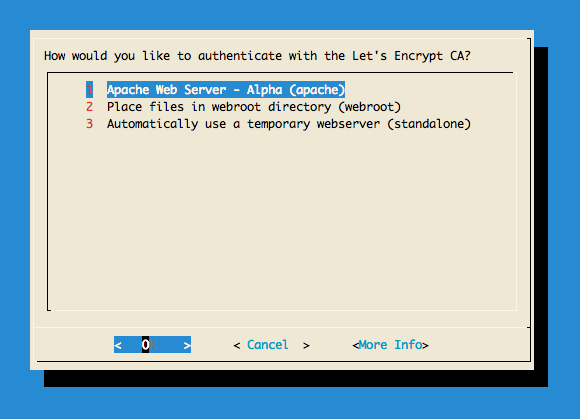
IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at /etc/letsencrypt/live/wowdoge.com/fullchain.pem. Your cert will expire on 2017-04-23. To obtain a new or tweaked version of this certificate in the future, simply run certbot-auto again. To non-interactively renew *all* of your certificates, run "certbot-auto renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
The magic has happened: Certbot has created all necessary keys and your free SSL certificates files. We are going to configure ISPConfig to use the certificate.
Configuring SSL in ISPConfig
Open the ISPConfig control-panel, go to sites, open the relevant website and enable the SSL checkbox.
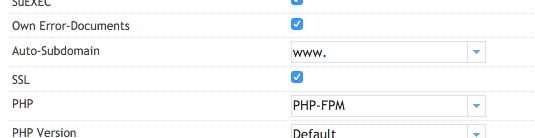
Now go the the SSL tab. We need to copy the obtained certificates and keys to these fields:
SSL Key: privkey.pem
Execute cat /etc/letsencrypt/live/wowdoge.com/privkey.pem and copy the contents to the field in ISPConfig.
SSL Certificate: cert.pem
Execute cat etc/letsencrypt/live/wowdoge.com/cert.pem and copy the contents to the field in ISPConfig.
SSL Bundle: chain.pem
Execute cat /etc/letsencrypt/live/wowdoge.com/chain.pem and copy the contents to the field in ISPConfig.
 Important: Select SSL Action ‘Save Certificate’
Important: Select SSL Action ‘Save Certificate’
Finally, have Apache redirect HTTP requests to HTTPS.
Method 1: Go to the Options tab and put the following in the Apache Directives field.
RewriteEngine on
RewriteCond %{SERVER_PORT} !^443$
RewriteRule ^.*$ https://%{SERVER_NAME}%{REQUEST_URI} [L,R=301]
Method 2: Go to Redirect tab and check Rewrite HTTP to HTTPS
Now the server is configured for this specific certificate. Select save and wait a minute or so for the configuration to become active.
Important: Let’s Encrypt certificates are only a couple of months valid and should be automatically renewed. See the next section for more info.

Enabling automatic periodical renewal
Certificates issued by Certbot have relatively short validity. Renewing a certificate however is easy. When a certificate is renewed it will be placed under /etc/letsencrypt/domain.com . We do not want to copy the certificates and keys every time we have to renew. Luckily there is an easy solution to this.
We are going to create symbolic links to help ISPConfig use the certificates directly generated in the /etc/letsencrypt directory. Go to the SSL directory of your site and create the following links (you might need to do this as super-user, sudo):
cd /var/www/wowdoge.com/ssl ln -sf /etc/letsencrypt/live/wowdoge.com/fullchain.pem wowdoge.com.crt ln -sf /etc/letsencrypt/live/wowdoge.com/privkey.pem wowdoge.com.key
Note: first just copy-paste the certificates and keys into ISPConfig. This is required for ISPConfig to configure the Apache correctly.
Create a renew-script, this is based on Let’s Encrypt example:
#!/bin/sh
service apache2 stop
/home/yourname/Certbot/certbot-auto renew -nvv --standalone > /var/log/letsencrypt/renew.log 2>&1
LE_STATUS=$?
service apache2 start
if [ "$LE_STATUS" != 0 ]; then
echo Automated renewal failed:
cat /var/log/letsencrypt/renew.log
exit 1
fi
Save it in for example your home-directory as renew-letsencrypt.sh and make it executable:
chmod +x renew-letsencrypt.sh
Now periodically call this script using CRON as root:
sudo crontab -e
Add the following line to call the renewal script every firstServer of the month at 4-o-clock.
00 04 01 * * /home/yourname/renew-letsencrypt.sh
Save your crontab and you’re ready to go!
Conclusion
That’s it! I am currently running multiple websites using Let’s Encrypt without any problems at all. Their free SSL certificates are trusted by almost all modern browsers and a lot of other applications that use SSL encryption.
Sponsored content
Frequently Asked Questions
OSError: Command /home/user/…./bin/python2.7 – setuptools pkg_resources pip wheel failed with error code 1
This error seems to happen when the localization codes are not set in your environment. Set them once by executing:
export LC_ALL="en_US.UTF-8" export LC_CTYPE="en_US.UTF-8"
Set them forever by adding these lines to your shell initialization script (.zshrc, .bashrc).
Is there a manual for ISPConfig?
ISPConfig 3.1: The official manual by the creators of ISPConfig